Network Security and Server Insurance: What You Need

In the realm of Network Security and Server Insurance: What You Need, readers are drawn into a world of crucial information designed to safeguard data effectively. This introduction sets the stage for a comprehensive exploration of key concepts and practical applications in the realm of cybersecurity and insurance.
The subsequent paragraphs delve into specific measures, coverage details, risk assessment strategies, data protection practices, legal considerations, and more, offering a well-rounded view of the topic.
Overview of Network Security and Server Insurance
Network security plays a crucial role in safeguarding sensitive data and information from unauthorized access, cyber attacks, and other potential threats. It involves implementing various measures to protect the integrity, confidentiality, and availability of data stored on networks.
Server insurance, on the other hand, serves as a financial safety net in the event of server failures, data breaches, or other unforeseen incidents that could result in significant losses for businesses. It helps mitigate risks associated with server downtime, data loss, and potential liabilities.
Examples of Potential Threats Addressed by Network Security and Server Insurance
- Malware: Network security measures such as firewalls and antivirus software help prevent malware infections that can compromise data integrity and disrupt operations.
- Data Breaches: Implementing encryption protocols and access controls can help prevent unauthorized access to sensitive information, reducing the risk of data breaches.
- Server Failures: Server insurance provides coverage for hardware failures, ensuring that businesses can recover quickly and minimize downtime in the event of server crashes.
- Ransomware Attacks: Network security measures like regular data backups and security patches help protect against ransomware attacks that can encrypt data and demand payment for decryption.
Network Security Measures
In today's digital age, ensuring the security of your network is crucial to protect sensitive data and prevent cyber threats. Implementing effective network security measures can help safeguard your organization from potential risks and vulnerabilities.
Firewalls, Antivirus Software, and Encryption
- Firewalls act as a barrier between your internal network and external threats, monitoring and controlling incoming and outgoing traffic based on predefined security rules.
- Antivirus software helps detect and remove malicious software like viruses, worms, and Trojans that can compromise the integrity of your network.
- Encryption is the process of converting data into a code to prevent unauthorized access, ensuring that even if data is intercepted, it remains unreadable to unauthorized users.
Intrusion Detection Systems (IDS)
Intrusion detection systems monitor network traffic for suspicious activity or potential security breaches. They analyze patterns and anomalies in network traffic to identify and alert system administrators of any unauthorized access attempts or malicious activities.
Regular Security Audits and Updates
- Regular security audits help identify vulnerabilities in your network infrastructure, applications, and systems, allowing you to address them proactively before they are exploited by cyber attackers.
- Keeping your security measures up to date with the latest patches and updates is essential to ensure that your network remains protected against new and evolving threats.
- By conducting routine security audits and applying timely updates, you can enhance the overall security posture of your network and reduce the risk of security incidents.
Server Insurance Coverage

Server insurance policies typically provide coverage for a range of risks and incidents that can impact the security and functionality of your servers. This coverage is essential to protect your business from potential financial losses and disruptions.
Types of Server Insurance Plans
There are different types of server insurance plans available in the market, each offering specific coverage options tailored to different needs. Some common types include:
- Hardware Coverage: This type of plan typically covers damages to the physical components of your server, such as hard drives, processors, and other hardware components.
- Software Coverage: This plan focuses on protecting your server from software-related issues, such as malware infections, data breaches, and software failures.
- Business Interruption Coverage: This type of coverage helps compensate for lost income and additional expenses incurred due to server downtime or disruptions.
- Data Recovery Coverage: This plan assists in recovering and restoring data in case of data loss or corruption on your server.
Scenarios Where Server Insurance Coverage is Beneficial
Server insurance coverage can be highly beneficial in various scenarios, such as:
- Protection Against Cyber Attacks: In the event of a cyber attack like ransomware or hacking, server insurance can help cover the costs of remediation, recovery, and potential legal liabilities.
- Hardware Failures: If your server experiences hardware failures that require repair or replacement, having server insurance can help mitigate the financial impact.
- Natural Disasters: Server insurance can provide coverage for damages caused by natural disasters such as floods, fires, or earthquakes, ensuring your business can recover quickly.
- Legal Compliance: Server insurance can assist in covering legal fees and penalties associated with data breaches or other compliance issues, helping your business stay protected.
Risk Assessment and Management

When it comes to ensuring network security and protecting your servers, conducting a thorough risk assessment is crucial. This process helps identify potential vulnerabilities and threats that could compromise your system.
Conducting a Risk Assessment
A risk assessment involves evaluating the likelihood of threats and the impact they could have on your network and servers. This includes identifying potential security gaps, weak points in the system, and the possible consequences of a security breach.
- Assess current security measures in place
- Identify potential vulnerabilities
- Evaluate possible threats and their impact
- Consider the likelihood of each threat
Managing Identified Risks
Once risks have been identified, it is essential to implement strategies to manage and mitigate them effectively. This proactive approach can help prevent security incidents and minimize the impact of any breaches.
- Implement security best practices and protocols
- Regularly update software and systems
- Train employees on security awareness
- Monitor network activity for unusual behavior
Integration of Server Insurance
Server insurance can be a valuable component of a comprehensive risk management plan. In the event of a security breach or data loss, server insurance can provide financial protection and support for recovery efforts.
- Include server insurance as part of risk mitigation strategy
- Review insurance coverage to ensure it aligns with security needs
- Understand the terms and conditions of the insurance policy
- Regularly assess and update insurance coverage based on changing risks
Data Protection and Backup Strategies
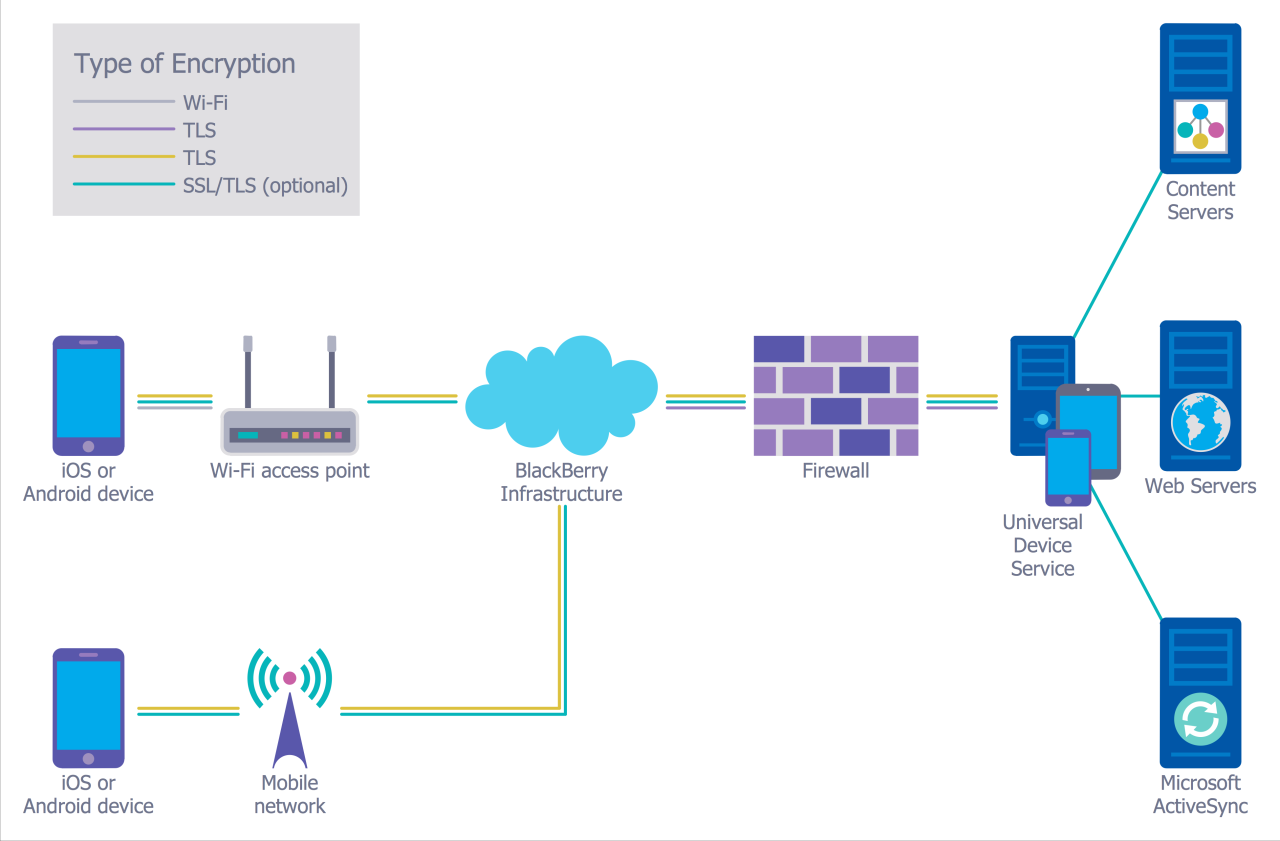
Data protection is a crucial aspect of network security, as it involves safeguarding sensitive information from unauthorized access, theft, or loss. Implementing effective data protection measures ensures the integrity and confidentiality of data within a network environment.
Importance of Data Backup
- Regular backups: Schedule frequent backups of data to ensure that the most up-to-date information is stored in a secure location.
- Offsite backups: Store backups in an offsite location to protect against physical damage or theft at the primary location.
- Automated backups: Utilize automated backup systems to streamline the process and reduce the risk of human error.
- Encryption: Encrypt backup data to add an extra layer of security and prevent unauthorized access.
Role of Server Insurance
Server insurance can play a critical role in recovering data in the event of a breach or server failure. In case of data loss, server insurance coverage can help cover the costs associated with data recovery efforts, minimizing the impact on business operations.
Legal and Compliance Considerations
When it comes to network security and server insurance, legal and compliance considerations play a crucial role in ensuring the protection of sensitive data and maintaining the trust of customers. Failure to comply with regulations can lead to severe consequences, both in terms of security breaches and insurance coverage.
Key Legal Requirements
- One of the key legal requirements related to network security is the General Data Protection Regulation (GDPR) in the European Union. This regulation aims to protect the personal data of individuals and imposes strict requirements on how organizations handle and secure this data.
- Another important legal consideration is the Health Insurance Portability and Accountability Act (HIPAA) in the United States, which sets standards for the protection of sensitive patient health information.
- Various industry-specific regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) for organizations that handle credit card information, also impact network security measures.
Compliance with Regulations
- Compliance with regulations like GDPR is essential for ensuring the security of sensitive data. Organizations must implement appropriate security measures, such as encryption and access controls, to protect personal information and avoid hefty fines for non-compliance.
- Failure to comply with regulations can not only result in legal consequences but also impact insurance coverage. Insurers may deny claims related to data breaches if organizations are found to be in violation of regulatory requirements.
Consequences of Non-Compliance
- Non-compliance with legal requirements can lead to data breaches, which can have severe repercussions on the reputation and financial stability of an organization. Customers may lose trust in the company, resulting in a loss of business.
- In terms of insurance coverage, non-compliance can void or limit the coverage provided by server insurance policies. This leaves organizations vulnerable to significant financial losses in the event of a security incident.
Closure
As we conclude our discussion on Network Security and Server Insurance: What You Need, it becomes evident that a robust security framework and comprehensive insurance coverage are indispensable in today's digital landscape. This summary encapsulates the essence of our exploration, emphasizing the critical role played by proactive security measures and risk management strategies.
Question & Answer Hub
What are the key legal requirements related to network security and server insurance?
Answer: Legal requirements may include compliance with data protection laws, industry regulations, and specific guidelines for safeguarding sensitive information. It is essential to stay informed about relevant laws to ensure adequate protection and compliance.
How can server insurance be integrated into a comprehensive risk management plan?
Answer: Server insurance can be integrated by assessing potential risks to server infrastructure, determining coverage needs, and aligning insurance policies with overall risk mitigation strategies. This ensures that server-related risks are adequately addressed within the broader risk management framework.
What role does data backup play in network security?
Answer: Data backup is crucial in network security to prevent data loss due to cyber threats, system failures, or human errors. Implementing robust backup strategies ensures that critical data can be restored in case of emergencies, contributing to overall data protection and business continuity.
How do intrusion detection systems enhance network security?
Answer: Intrusion detection systems monitor network traffic for suspicious activities or anomalies that may indicate a security breach. By promptly detecting and alerting on potential threats, these systems enhance network security by enabling timely response and mitigation actions to prevent data compromise.

